While we all might be aware of cybersecurity, there is considerable confusion as to what it actually is, and who it serves to protect. Much of the media conversation around cybersecurity is couched in the language of protecting state interests against “bad players” in the digital ecosystem, such as hackers. The standard media depiction of hackers are as shady individuals lurking in a maze of binary, leveraging their expertise to target the innocent and the vulnerable.
The messaging of the state is that it can protect you only if you expose all your data to its paternalistic patronage, positioning itself as a safe haven and trusted repository with the citizen’s interests at heart. Ideally, however, cybersecurity should be inextricable from individual privacy, and be exercised as a human right. This sets up an opposition between privacy and (state) security, the latter a state mandated diktat which undermines rather than enforces individual privacy.
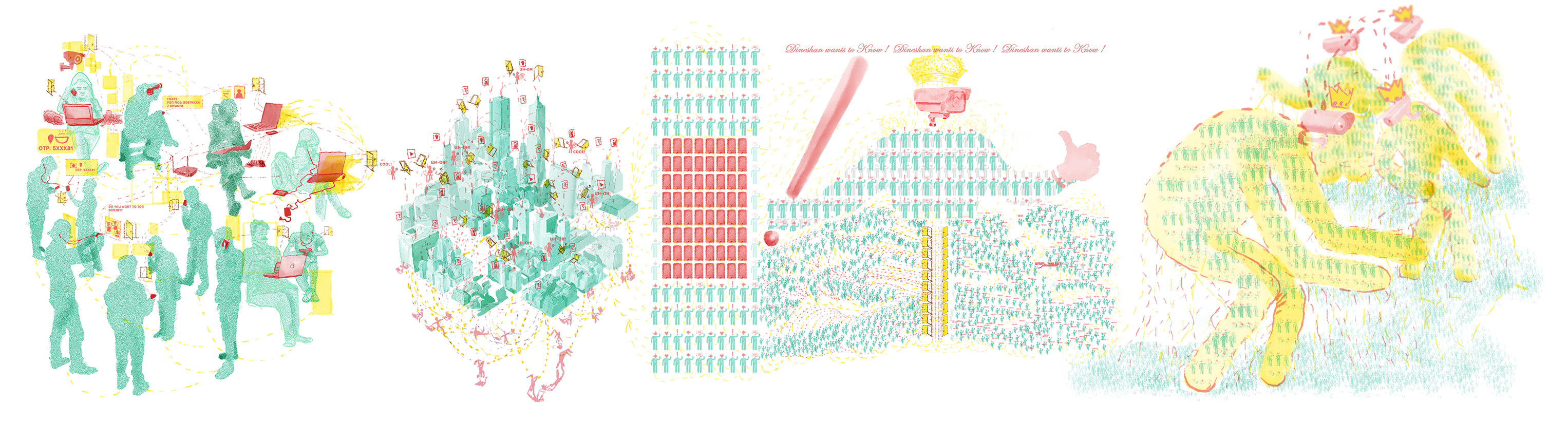
The ideal way to understand the relationship between the two is that privacy can lead to better security. In our illustrations, we have tried to decode and respond to the assumptions that underpin commissioning of illustrations of cybersecurity for the mainstream media. The way cybersecurity is traditionally illustrated, through tropes of closed locks, glowing green “leetspeak” emblazoned on dark backgrounds against which hooded anonymous figures on keyboards ostensibly plot the downfall of democracy, reiterates the state narrative that all cybersecurity practices are dangerous to the citizen, thus creating a blanket paranoia of these exercises, many of which actually work towards safeguarding citizen privacy rather than destroy
There is a lack of attention often paid to editorial illustrations and representations in Indian media houses, a shortcoming which has been further exacerbated by the easy availability of stock images. These are often inserted into articles without much forethought or attention paid to the content of the article that they accompany. Some of this indifference is a consequence of a lack of insight into the nuances of cybersecurity, thus flattening the visual narrative by resorting to easy tropes which circulate readily in an online economy funded by image search banks.
These illustrations were originally conceived as challenging these tropes by moving away from them completely; however, it was through the reframing of existing tropes it became possible to deconstruct the assumptions that underpin much of these visuals.
The complexity of everyday technology use, social media, platform governance, consent and privacy, is a part of some of the narrative and can be seen, in this case, to manifest, by using old tropes - such as icons of keys, locks, doors, silhouetted characters in hoodies, footprints, screens, mines, lines of code-leaking, magnifying glasses, finger prints, eyes, cameras, hooks, fishes and the odd badge with chains - taking them out of context, subverting them and sometimes the amplification of older meanings at newer scales. There is an effort to show the intended manifestations of technology in the form of physical gestures, ephemeral experiences, imagined and realized services and the very real physical infrastructures alongside the very actual humans and their data. The research underpinning these illustrations have also been about play, how devising a playframe to say or show things that might otherwise be difficult to transition through text, or to see both in detail and as a whole or might seem ludicrous. Some of these manifest when the unintended networking of many of these services allows for incredibly unregulated flow and access of data and more so the metadata trails from these intended technologies.
What follows from the first panel up till the last, is a depiction of interactions, that may be understood as behaviors around and through digital technologies,that allow for networked computer mediation, at various scales.

The Handbook concept, content and design by Padmini Ray Murray and Paulanthony George from Design Beku. With constant inputs from the CIS team Saumyaa Naidu, Shweta Mohandas and Arindrajit Basu. We would also like to thank Karan Saini for his invaluable inputs that helped us commission this publication.
We thank the Hewlett Foundation for funding this research.
Published by The Centre for Internet and Society, India | cis-india.org.